
Volume 2 - Attachment 7
BSS Risk Management
Framework Plan
Final Proposal Revisions
Enterprise Infrastructure
Solutions (EIS)
The original document was submitted as Harris Corporation, prior to
becoming L3Harris Technologies. The following pages are as submitted.

Government Communications Systems
Solicitation No.: QTA0015THA3003
04 November 2016
Volume 2—Attachment 7 - BSS Risk Management Framework Plan
Final Proposal Revisions
Enterprise Infrastructure Solutions
(EIS)
For:
General Services Administration/FAS/ITS
Office of Acquisition Ops
1800 F Street, NW
Washington, DC 20405
Attention:
Timothy Horan
Contractor Bid or Proposal information - See FAR 3.104. This proposal or quotation includes data that shall not be
disclosed outside the Government (or in the case of a proposal submitted to a Prime contractor, outside the Prime or
the Government) and shall not be duplicated, used or disclosed- in whole or in part- for any purpose other than to
evaluate this proposal or quotation. If, however, a contract is awarded to this offeror or quoter as a result of- or in
connection with- the submission of this data, the Government shall have the right to duplicate, use or disclose the data
to the extent provided in the resulting contract. This restriction does not limit the Government’s right to use information
contained in this data if it is obtained from another source without restriction. The data subject to this restriction are
contained in sheets or displayed on screens as marked. This document or electronic file contains Harris Corporation
proprietary information, which is exempt from disclosure under the Freedom of Information Act (5 USC 552). See FAR
24.202. Copyright 2016, Harris Corporation.

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
o
f this Proposal document or electronic file. This document or electronic file contains contractor trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
ii
TABLE OF CONTENTS
Paragraph Title Page
1.0 INTRODUCTION ................................................................................. 2-7-1
1.1 Purpose ............................................................................................... 2-7-2
2.0 RISK MANAGEMENT FRAMEWORK PROCESS...............................2-7-2
3.0 STEP 1 – CATEGORIZE THE INFORMATION SYSTEM ................... 2-7-3
3.1 Information System Description ........................................................... 2-7-4
3.1.1 Name and Contact Information for the Information System Owner...... 2-7-5
3.1.2 Location of the Information System ..................................................... 2-7-5
3.2 Status of the Information System......................................................... 2-7-6
3.3 System Boundaries..............................................................................2-7-6
3.4 System Security Plan...........................................................................2-7-7
4.0 STEP 2 - SELECT SECURITY CONTROLS ....................................... 2-7-8
4.1 Security Control Selection....................................................................2-7-9
4.2 Common Security Controls ................................................................ 2-7-13
4.3 Hybrid Security Controls .................................................................... 2-7-15
4.4 System Specific Security Controls ..................................................... 2-7-16
4.4 Tailoring the Baseline Controls .......................................................... 2-7-18
4.5 Monitoring Strategy............................................................................2-7-18
4.6 Security Plan Approval....................................................................... 2-7-19

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
o
f this Proposal document or electronic file. This document or electronic file contains contractor trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
iii
TABLE OF CONTENTS (continued)
Paragraph Title Page
5.0 .............................2-7-19
5.1 Security Control Implementation........................................................ 2-7-19
5.2 Security Control Documentation ........................................................ 2-7-20
6.0 .................................... 2-7-22
6.1 Assessment Preparation....................................................................2-7-22
6.2 Scanning and Penetration Testing.....................................................2-7-23
6.3 Security Control Assessment............................................................. 2-7-24
6.4 Security Assessment Report.............................................................. 2-7-25
6.5 Remedial Actions............................................................................... 2-7-26
7.0 ................... 2-7-26
7.1 Security Authorization Package .........................................................2-7-27
7.2 Plan of Action and Milestones............................................................ 2-7-27
7.3 Risk Determination and Acceptance.................................................. 2-7-29
8.0
SECURITY CONTROLS....................................................................2-7-29
9.0 ACTIVITY SCHEDULE ...................................................................... 2-7-30

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
o
f this Proposal document or electronic file. This document or electronic file contains contractor trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
iv
LIST OF ILLUSTRATIONS
Figure Title Page
1.0 The NIST RMF Lifecycle, per NIST SP 800-37....................................2-7-1
2.0 Alignment of the SDLC phases with the RMF Phases......................... 2-7-2
3.2 The Functional Architecture of the BSS,
within the Context of the EIS Mission and Operations ........................2-7-5
3.3 Interconnection Boundaries of the BSS ............................................... 2-7-6
4.0 The Relationship Between Common, Hybrid,
and System Specific Controls and the Authorization Decision............. 2-7-9
6.0 Security Control Assessment Process............................................... 2-7-22
8.0 Continuous Monitoring Activities........................................................ 2-7-30
9.0 Task Schedule to Obtain Authorization and Approval –
Business Support Services ................................................................2-7-31
LIST OF TABLES
Table Title Page
3.0 The Harris BSS Solution Provides a Robust Functionality Set
Covering all the Required and Highly Desired Optional Functions ...... 2-7-3
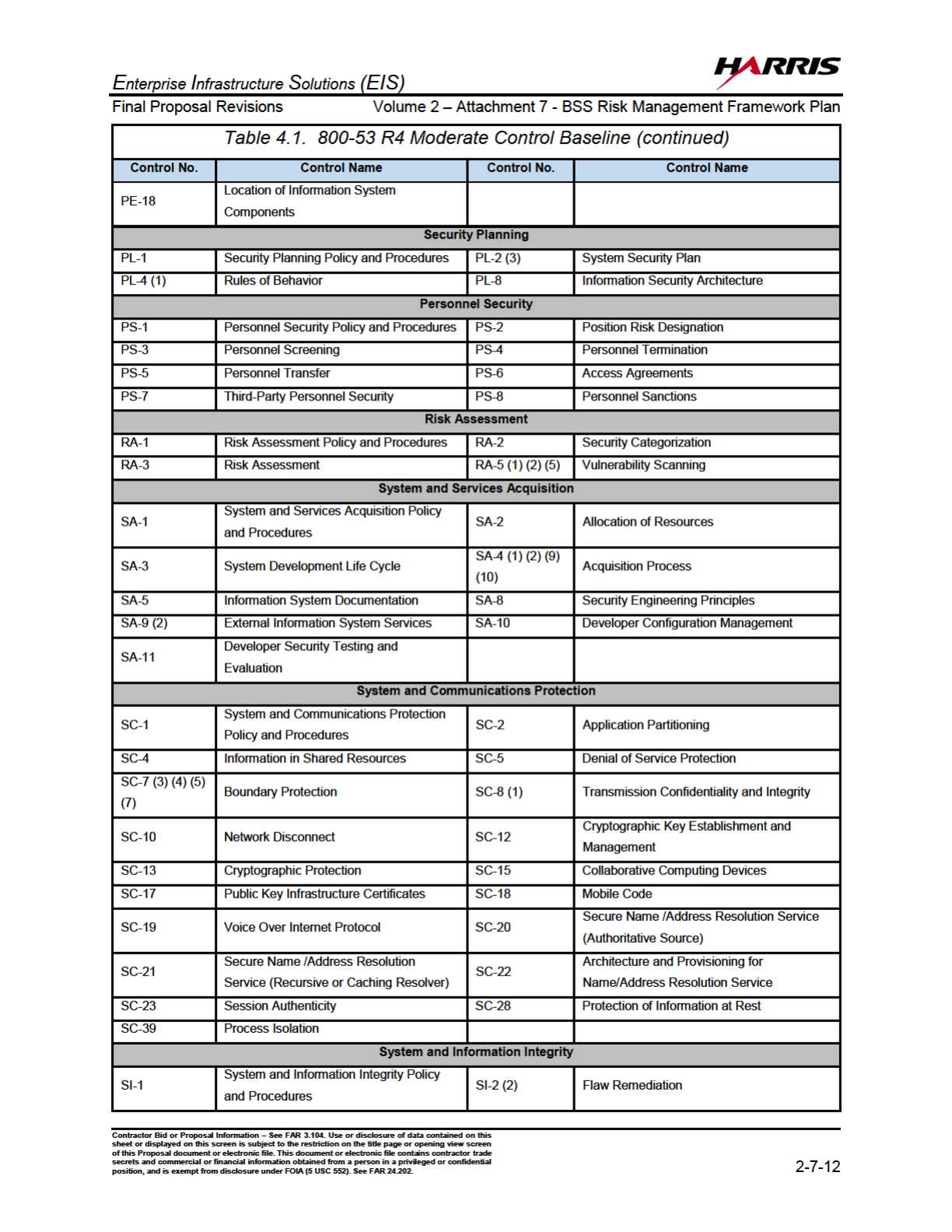
4.1 800-53 R4 Moderate Control Baseline...............................................2-7-10
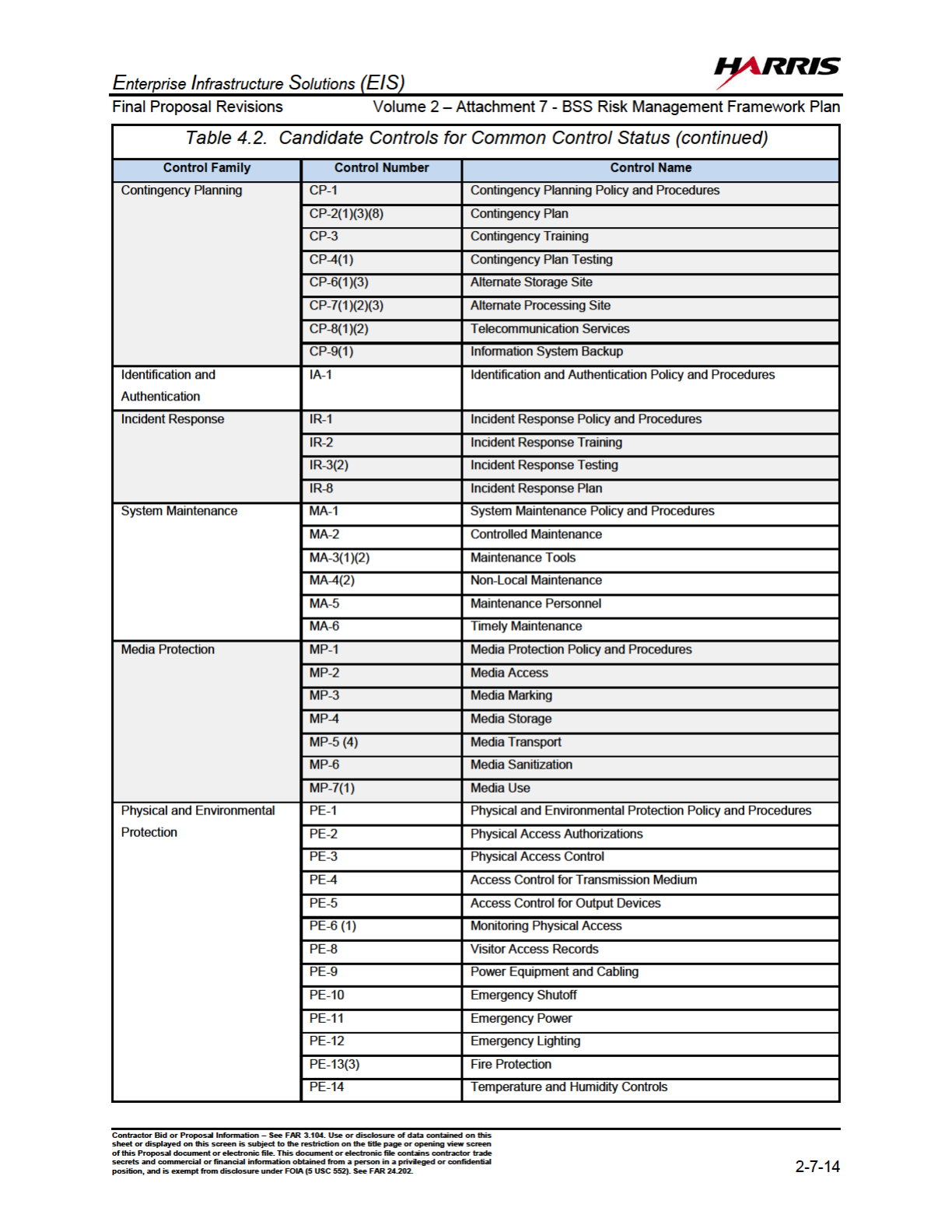
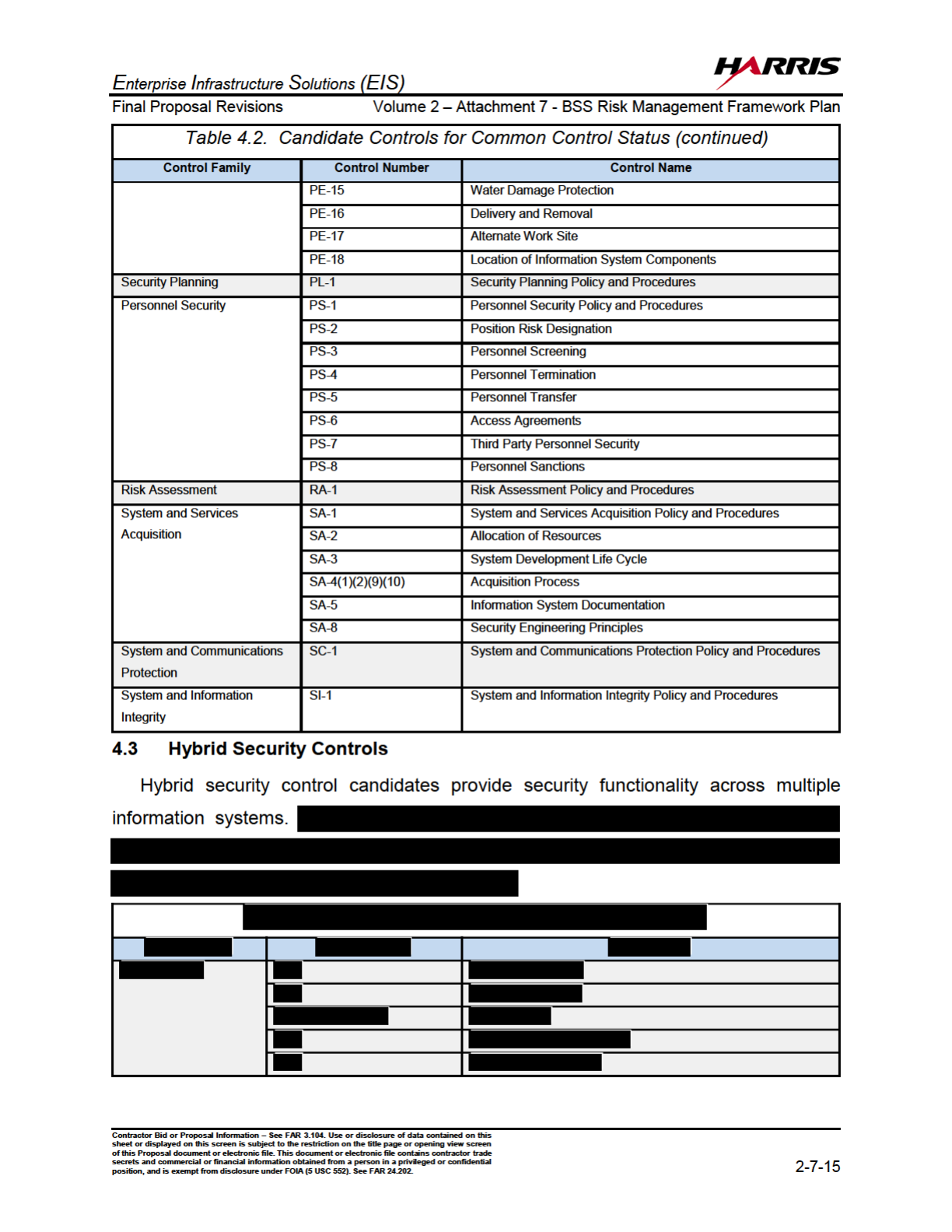
4.2 Candidate Controls for Common Control Status................................2-7-13
4.3 Candidate Controls for Hybrid Control Status ....................................2-7-15
4.4 Candidate Controls for System Specific Control Status..................... 2-7-16
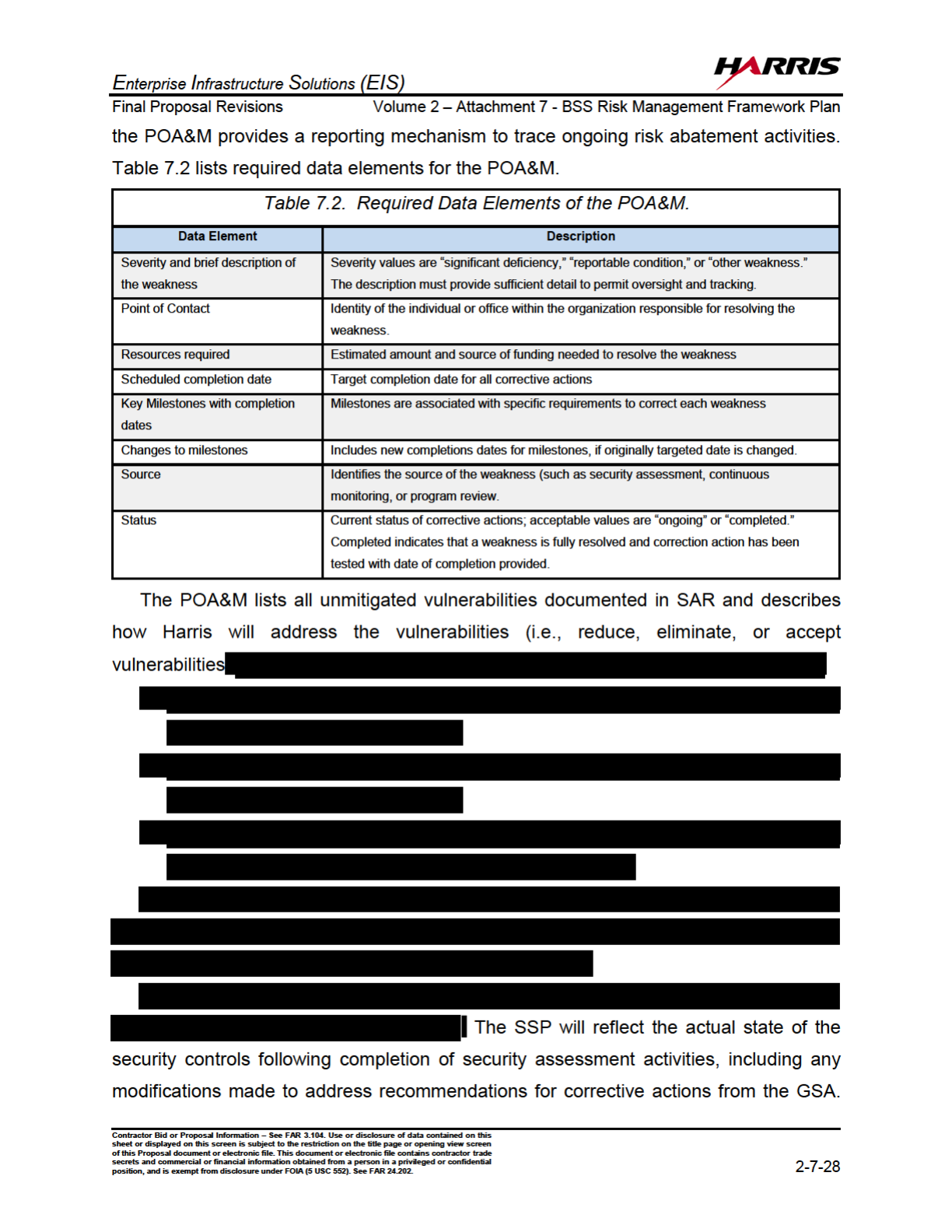
7.2 Required Data Elements of the POA&M. ...........................................2-7-28

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
o
f this Proposal document or electronic file. This document or electronic file contains contractor trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
v
LIST OF ACRONYMS
A&A Assessment and Authorization
AC Access Control
AO Authorizing Official
ATO Authorization to Operate
AU Audit and Accountability
BNOC Backup Network Operations Center
BSS Business Support System
C&A Certification and Accreditation
CP Contingency Planning
FCCI Federal Cloud Computing Initiative
FISMA Federal Information Security Management Act
GFP Government Furnished Property
HTEN Harris Trusted Enterprise Network
IDIA Identification And Authentication
IPVS IP Voice Services
IR Incident Response
ISSM Information System Securtiy Manager
KPIs Key Performance Indicators
MA Maintenance
MANs Metro Area Networks
MNS Managed Network Services
MPLS Multiprotocol Label Switching
NIST National Institute of Standards and Technology
OSAISO Office of the Senior Agency Information Security Officer
PE Physical and Environmental
POA&M Plan of Action and Milestones
POP Point of Presence
PS Personnel
PSTN Public Switched Telephone Network

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
o
f this Proposal document or electronic file. This document or electronic file contains contractor trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
vi
LIST OF ACRONYMS (continued)
RA Risk Assessment
RFP Request for Proposal
RMF Risk Management Framework
SC System and Communications Protection
SCAP Secure Content Automation Protocol
SDLC System Development Life Cycle
SDP Service Delivery Point
SI System and Information Integrity
SRE Service Related Equipment
SRL Service Related Labor
SSP System Security Plan
VoIP Voice Over Internet Protocol
VPN Virtual Private Network
WAN Wirelss Area Network

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
1
1.0 INTRODUCTION
This Risk Management Framework (RMF) Plan explains how the Business Support
Systems (BSS) implement the RMF life cycle as defined in NIST Special Publication
800-37, “Guide for Applying the Risk Management Framework to Federal Information
Systems: A Security Life Cycle Approach”. The BSS provides the daily operational
infrastructure required to order, and provision services, status the health of the system,
and reconcile customer billing and adherence to Service Level Agreements and Key
Performance Indicators (KPIs).
The Risk Management Framework, illustrated in Figure 1.0, integrates the security life
cycle with the risk life cycle of the system development process.
Figure 1.0. The NIST RMF Lifecycle, per NIST SP 800-37
The Federal Information Security Management Act (FISMA) of 2002, states that any
IT system that stores, transports or processes Federal Government data requires a formal
approval process known as security Assessment and Authorization (A&A) (formerly





Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
7
3.4 System Security Plan
Harris will develop a BSS System Security Plan (SSP) that describes the information
system (including system boundary) based on guidance from NIST SP 800-18 R1, “Guide
for Developing Security Plans for Federal Information Systems.” The GSA SSP template
is defined in GSA Information Technology (IT) Security Policy, CIO P 2100.1(J). The BSS
SSP will provide an overview of the BSS security requirements and will describe the
security controls in place or planned to address those requirements. Descriptive
information about the information system is documented in sections 1-5 of the SSP,
following the GSA SSP template. The BSS SSP will include the following sections based
on the GSA SSP template:
- System Identification
- Information System Categorization
- BSS Roles and Responsibilities
- BSS Operational Status
- Information System Type
- General System Description/Purpose
- System Interconnections and Interfaces
- Laws, Regulations, Policies and Guides Affecting the Federal Use of the BSS
- Cloud Controls (if applicable)
- Management Controls
o Security Assessment and Authorization (CA)
o Planning (PL)
o Risk Assessment (RA)
o System and Services Acquisition (SA)
- Operational Controls
o Security Awareness and Training (AT)
o Configuration Management (CM)
o Contingency Planning (CP)
o Incident Response (IR)
o Maintenance (MA)
o Media Protection (MP)

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
8
o Physical and Environmental (PE)
o Personnel (PS)
o System and Information Integrity (SI)
- Technical Controls
o Access Control (AC)
o Audit and Accountability (AU)
o Identification and Authentication (IA)
o System and Communications Protection (SC)
- Appendices for supporting documentation
3.5 Information System Registration
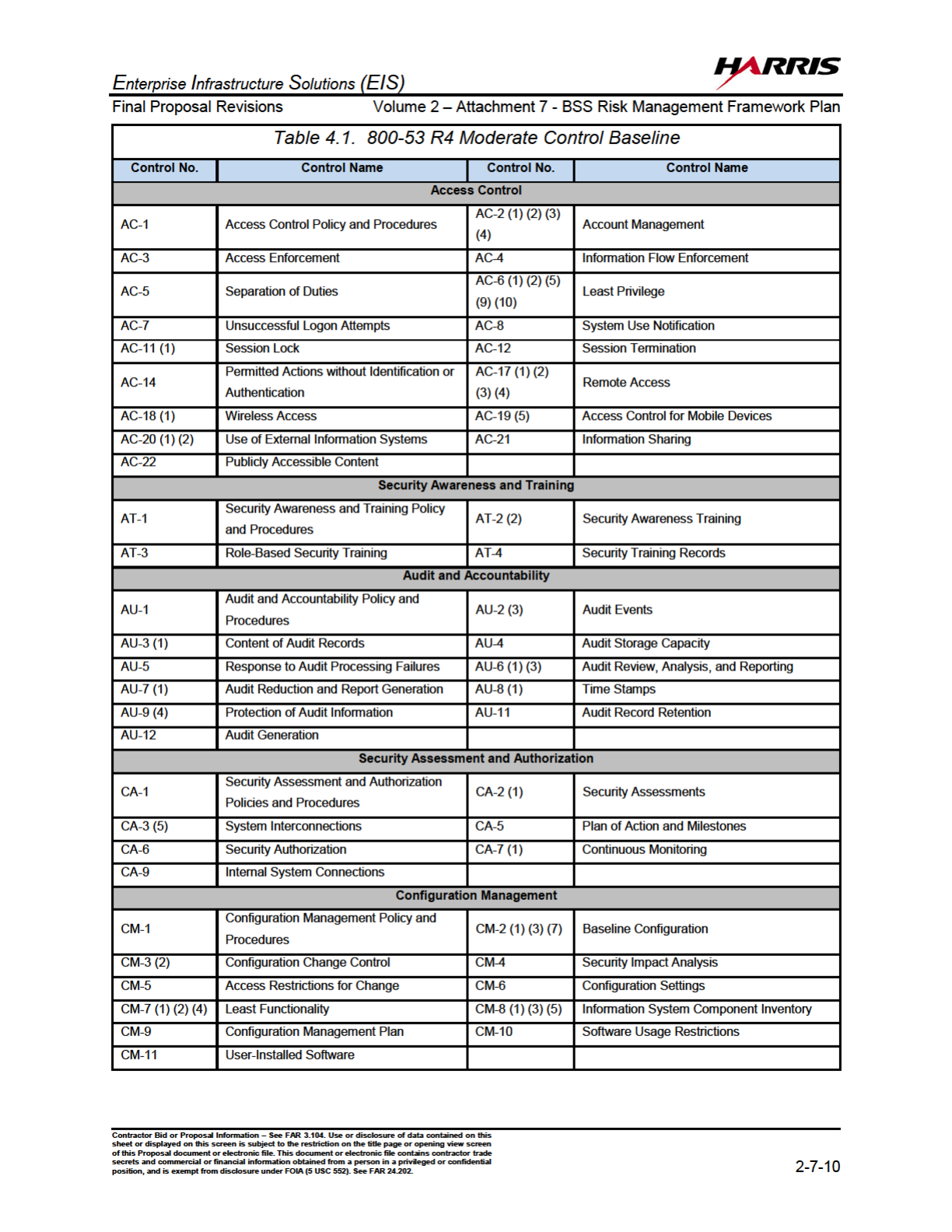
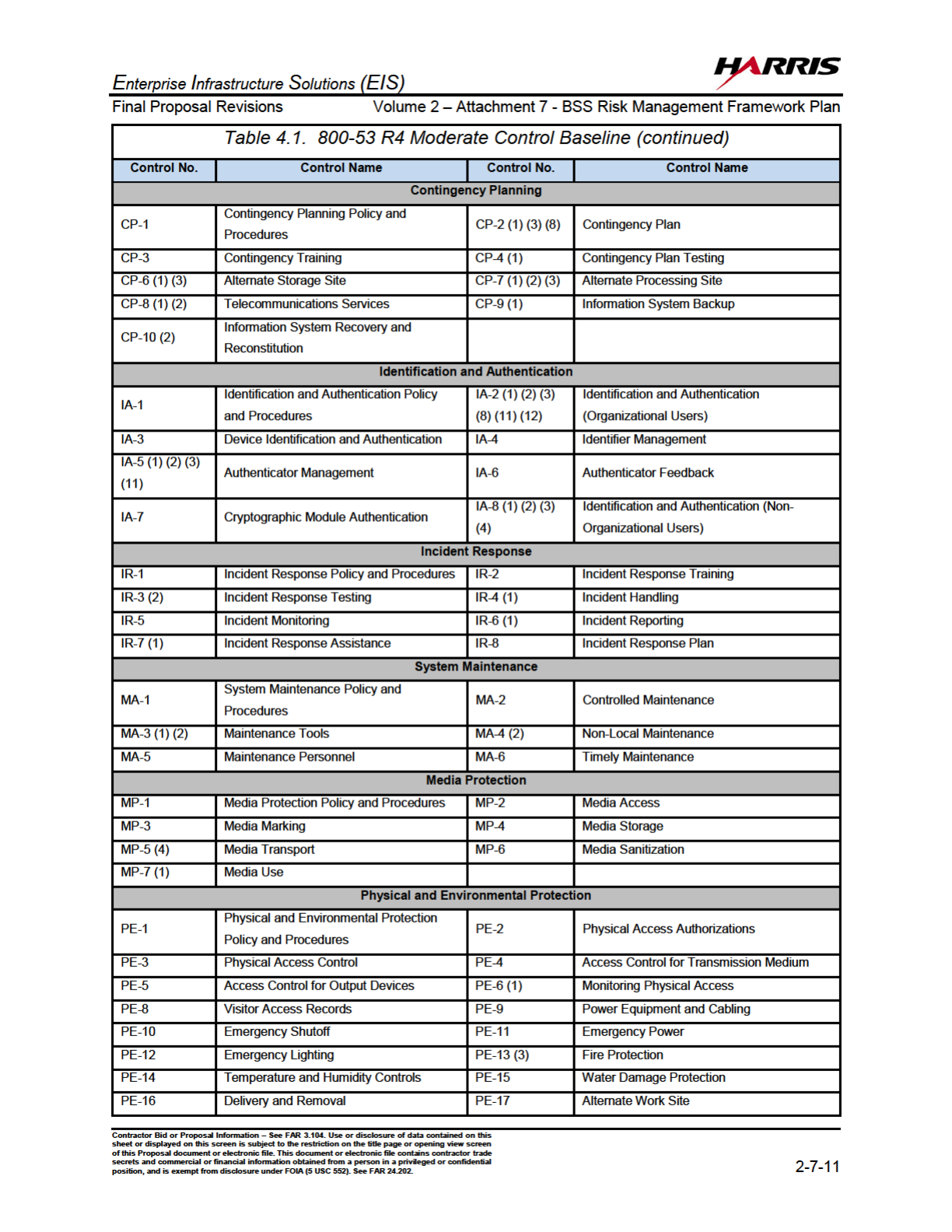
4.0 STEP 2 - SELECT SECURITY CONTROLS
Based on the FIPS 199 Impact Level of “Moderate” that was determined for the BSS,
GSA selected the baseline of security controls for the BSS as defined in FIPS 200,
“Minimum Security Requirements for Federal Information and Information Systems” and
the companion guide NIST 800-53 R4 “Minimum Security Controls for Federal Information
Systems.
Security controls are categorized as:
(i) system-specific controls (i.e., controls that provide a security capability for a
particular information system only);
(ii) common controls (i.e., controls that provide a security capability for multiple
information systems); or
(iii) hybrid controls (i.e., controls that have both system-specific and common
characteristics).





Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
20
5.2 Security Control Documentation
Harris will document the security control implementation in the BSS SSP. This will
provide a functional description of the control implementation (including planned inputs,
expected behavior, and expected outputs), using the GSA SSP template. Security
controls are documented in Sections 3-5 of the SSP and are presented per the
requirements in NIST 800-18 R1. For each control the following documentation template
will be used:
Security control name and requirement text with GSA-defined settings
Control type (Enterprise Common, System Common, Hybrid, System Specific,
Inherited, N/A)
Implementation Status (In-Place, Partially In-Place, Planned, N/A)
Asset group applicability
Description of how the security control is implemented
The completed SSP will include the following supporting documentation in appendices:
Rules of Behavior (Appendix B)
BSS Hardware and Software Inventory (Appendix C)
Security Control Tailoring Workbook (Appendix D)
Continuous Monitoring Plan (Appendix E)
Privacy Impact Statement (Appendix F)
Security Assessment Boundary and Scope Document (Appendix G)
GSA Control Summary Table (Appendix H)
Configuration Management Plan (Appendix I)
Includes the BSS System Baseline Configuration Standard Document
Includes the System Configuration Settings documentation
Incident Response Plan (Appendix J)
Includes the Incident Response Test Report
Interconnection Security Agreements (ISA), MOAs and MOUs (Appendix K)
E-Authentication Documentation (Appendix L)
Contingency Plan (Appendix M)

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
21
Includes Contingency Plan Test Plan and Test Report
Includes Disaster Recovery Plan
Business Impact Assessment (Appendix N)
Security Awareness and Training Plan (Appendix O)
Additional supporting documentation to be provided with BSS SSP:
Policies and Procedures
Access Control
Security Awareness and Training
Audit and Accountability
Security Assessment and Authorization
Configuration Management
Contingency Planning
Identification and Authentication
Incident Response
System Maintenance
Media Protection
Physical and Environmental
Security Planning
Personnel Security
Risk Assessment
Systems and Services Acquisition
System and Communications Protection
System and Information Integrity
The updated SSP formalizes plans and expectations regarding the overall functionality
of the BSS. The SSP will address any platform dependencies and describe how the
security control is achieved at the level of detail required to support the security control
assessment phase.


Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
23
The Security Assessment Plan will be developed according to GSA guidelines and the
template provided in Appendix A of GSA CIO Security Procedural Guide 06-30. The
assessment plan template includes the following sections:
Introduction – system background information
Methodology – assessment approach, evaluation criteria, test schedule, team,
resources, etc.
System Characterization – description of system being tested
Assessment Test Cases
6.2 Scanning and Penetration Testing
As stated in GSA IT Security Procedural Guide 11-51, “Conducting Penetration Test
Exercises”, Penetration or Pen Testing techniques provide a final assurance test for the
operational configuration of the BSS.


Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
25
The goal of the assessment is to determine if the security controls implemented in the
previous phase are operating as intended and producing the desired outcome with
respect to meeting the security requirements for the BSS.
6.4 Security Assessment Report
Once the security assessment activities have been completed the issues, findings,
and recommendations are documented. A given security control test case either fully
meets the objective, partially meets the objective, or fails.
The GSA (or its representative) will document assessment findings with
recommendation(s) and risk determinations from the NIST 800-30 risk assessment
process in a Security Assessment Report using the template in Appendix B of GSA CIO
Security Procedural Guide 06-30. The report identifies any Critical, High and Moderate
operating system, web application, and database scan/configuration vulnerabilities. The
Security Assessment Report will contain results of the completed assessment test cases
as well as the results of any vulnerability scans performed.
Using the Security Assessment Report as input, a risk analysis report will be prepared
to determine the security risk associated with operating the system. The security risk is
analyzed for both individual test case findings and the overall BSS security posture. The
risk determination will be included as part of the authorization package. Per GSA CIO
Security Procedural Guide 06-30, the risk assessment will consist of one or more of the
following activities:

Enterprise Infrastructure Solutions (EIS)
Final Proposal Revisions Volume 2 – Attachment 7 - BSS Risk Management Framework Plan
Contractor Bid or Proposal Information – See FAR
3.104. Use or disclosure of data contained on this
sheet or displayed on this screen is subject to the restriction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contractor
trade
secrets and commercial or financial information obtained from a person in a privileged or confidential
position, and is exempt from disclosure under FOIA (5 USC 552). See FAR 24.202.
2-7-
26
A list of threats to the system (hackers, malicious insiders, attacks against the
system facility, natural disasters, etc.) will be developed based on threat
information available to GSA.
Using the threat information, Vulnerability/Threat Pairings will be developed.
Each system instance of absent controls and/or vulnerabilities identified during the
Security Assessment will be assessed to evaluate the likelihood that one of the
identified threats will exploit an identified vulnerability.
The possible impact to the system and the GSA if the vulnerability was exploited
will be assessed and a determination of risk will be made on the likelihood that the
threat will exploit the vulnerability and the resulting impact.
The overall risk level of the BSS will be determined by evaluating the risks of all
identified vulnerabilities.
The Security Assessment Report will document any findings from the security
assessment that are not “Fully Satisfied” with vulnerability/threat pairing, in-place controls
discussion, likelihood, impact, and risk discussion/rating, and recommended
countermeasures for correcting deficiencies in security controls.
6.5 Remedial Actions
7.0 STEP 5 AUTHORIZE THE INFORMATION SYSTEM




tee Instructu Solutions (EIS)
Contractor Bid or Proposal lnfoation - See FAR 3.104. Use or disclosu of data contained on this
sheet or displayed on this scen is subject to the striction on the title page or opening view screen
of this Proposal document or electronic file. This document or electronic file contains contctor trade
sects and commercial or financial infoation obtained from a peon in a privileged or confidential
s
2-7-31


